After spending 14 years as the good guy in cybersecurity (the blue teamer who makes sure everything is secure), I decided it was time to walk on the wild side. I grabbed myself a copy of Kali Linux, a stack of ethical hacking books, and signed up for a couple of courses. I was all set to dive into the shadowy depths of red teaming. I never realized MAC Spoofing was so easy.
The Plot Thickens: Why Not Stir Things Up a Bit?
One evening, while Antonio was lost in the world of spreadsheets and emails, I figured it was the perfect time to test my new skills—and maybe play a prank to grab his attention. What better way to do this than a little harmless MAC spoofing? I mean, what could possibly go wrong, right?
The Setup: A Fun Attempt at MAC Spoofing
Here’s the lowdown: Think of MAC spoofing as your device donning a disguise. It’s like swapping out the license plate on your car for another one—except in this case, the car is your computer, and the license plate is the MAC address, a unique identifier that network devices use to communicate on a local network. My brilliant (or so I thought) plan? I decided to switch my MAC address to mirror Antonio’s laptop’s MAC. I figured it might cause a slight glitch on his end, just enough to steal a glance from him. Well, let’s just say it turned into a bit more of an event than I anticipated!
Different Attacks Enabled by MAC Spoofing
MAC spoofing isn’t just about causing a little harmless chaos on your home network. When in the wrong hands (or sometimes even the right hands at the wrong time), it can be used for a variety of crafty and sometimes malicious activities:
- Network Intrusion: By masquerading as a known device, a hacker can gain unauthorized access to a restricted network. This is like getting past the bouncer by wearing a disguise.
- Denial of Service (DoS): Just like my little experiment, spoofing the MAC address of another device can lead to network conflicts that disrupt services, effectively knocking users off the network.
- Man-in-the-Middle (MitM) Attacks: By changing their MAC address to match that of a device involved in a communication session, a hacker can intercept and possibly alter communications between two parties without either party knowing.
- Bypassing MAC Address Filters: Some networks restrict access to specific MAC addresses. By changing their MAC to one that is whitelisted, an intruder can bypass these filters and access the network.
- Connection Poisoning: In environments where devices trust each other based on MAC addresses, spoofing can be used to poison the connection or inject malicious data into the network.
- Evading Detection and Bypassing Bans: If a device is banned from a network based on its MAC address, changing the MAC address allows the banned device to regain access, effectively evading detection and the original ban.
MAC spoofing, as you can see, is a versatile tool in the cyber trickster’s toolkit—perfect for a variety of pranks and hacks, depending on how you swing it! Just remember, with great power comes great responsibility (and potentially great messes to clean up).
So, with Kali Linux fired up, I followed these not-so-complicated steps (which I’m about to share with you). My goal? To see if I could make his laptop do a double-take on the network.
How to Be a MAC Spoofing Wizard Using ifconfig
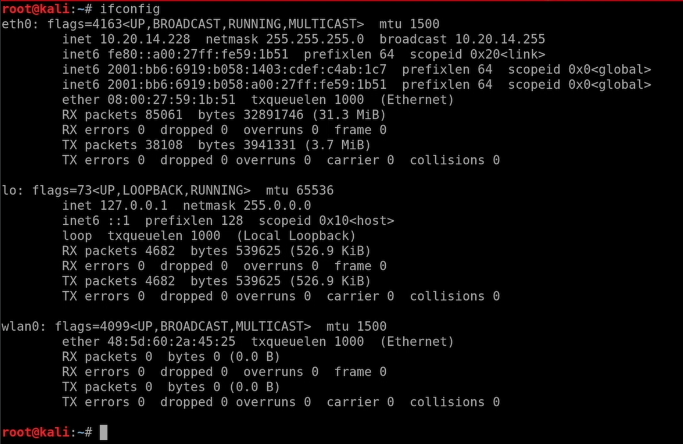
Alright, grab your wizard hats, folks. Here’s how you can try this at home (or anywhere really):
- Open Terminal: Hit
Ctrl + Alt + Tor just poke around in your applications menu until you find the Terminal. - Check Out Your Network Stuff:
sudo ifconfigLook for the name of the interface you want to use (like eth0 for wired or wlan0 for wireless). Take a mental snapshot of the current MAC address.
- Give the Network Interface a Little Nap:
sudo ifconfig wlan0 downSwap wlan0 with whatever your network card’s name is.
- Slip on the New MAC Address:
sudo ifconfig wlan0 hw ether XX:XX:XX:XX:XX:XXChange wlan0 and XX:XX:XX:XX:XX:XX to the actual interface name and the new MAC address you’re spoofing.
- Wake Up the Network Interface:
sudo ifconfig wlan0 up- Did It Work?:
sudo ifconfig wlan0Peek at the wlan0 line to see if the MAC address has really changed.
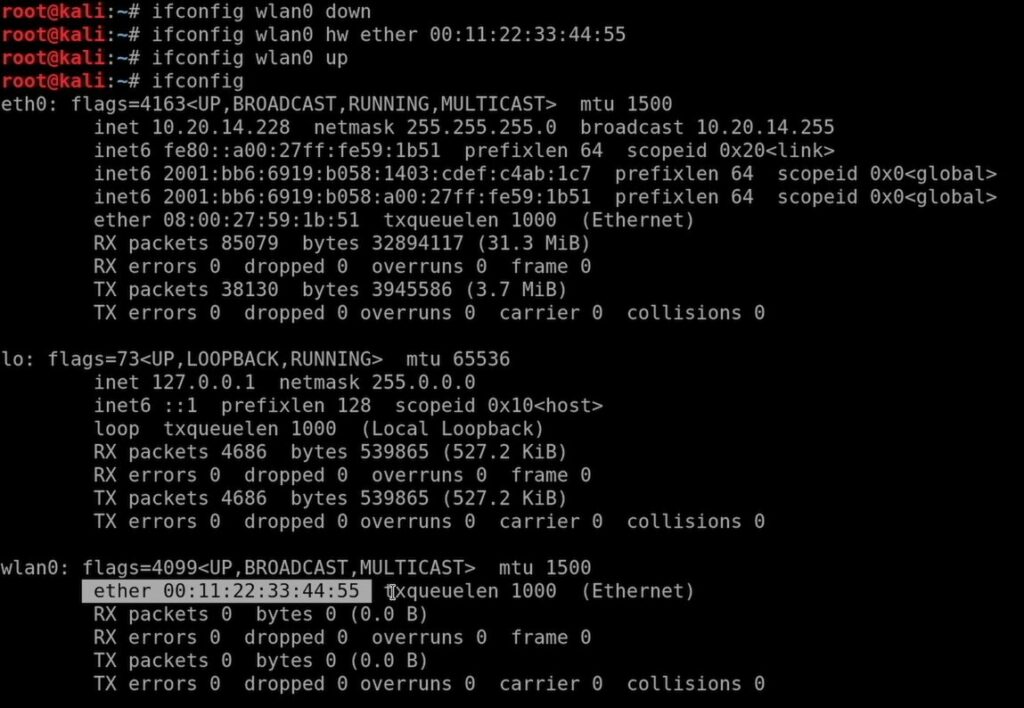
The Outcome: A Little Chaos, A Lot of Fun
Long story short, both our devices ended up battling it out for the network’s attention, causing a complete network meltdown for him (oops). Instead of getting annoyed, though, Antonio actually found it hilarious once he realized why his internet had vanished. After rebooting my device (this restores the computer to its original MAC address) and fixing the network mess I’d made, we ended up having a blast talking about cybersecurity, hacking, and the importance of not taking your network for granted.
The Moral of the Story
This little adventure not only spiced up our evening but also reminded us that playing around with network settings can lead to unexpected learning opportunities (and maybe a bit of chaos). It’s a fun reminder that every tool and trick in the world of cybersecurity can be a doorway to new insights—just maybe give your network a heads-up first!




Pingback: At-Home Cyberwar: A Guide to Deauthentication Attacks - Addie LaMarr
Pingback: WEP Cracking: Techniques for Accessing “Secure” Wi-Fi Networks - Addie LaMarr