In today’s digital world, sifting through vast data to find precise, actionable information can feel like searching for a needle in a haystack.
Whether you’re a cybersecurity expert, an investigative journalist, or someone trying to reconnect with a long-lost friend, the demand for reliable data is at an all-time high.
Enter Open Source Intelligence (OSINT), your key to unlocking the power of publicly available information.
Mastering OSINT techniques not only helps navigate this digital expanse but also transforms the way we uncover hidden or hard-to-find data, making it an indispensable skill in our interconnected world.
My Mission – A Dive into the World of OSINT
Let me take you back to a mission I was given in 2021, one that would dramatically shift my view of the digital world and introduce me to the game-changing power of OSINT.
Imagine this: You’re tasked with an assignment that seems straight out of a spy novel—identifying a man from nothing more than a blurry background figure in a photograph.
You have no name, no location, and no other information aside from this photograph.
This isn’t just a test of your curiosity; it’s a deep dive into a dilemma that plagues many of us in this age of information overload.
You’re confronted with the monumental challenge of extracting specific, actionable data from the endless digital sea.
The conventional methods of search you rely on turn up empty, offering mere scraps of surface-level information.
What do you do?

It feels like you’re navigating through an endless maze of irrelevant and unstructured data.
The usual Google searches or simple social media inquiries fall short, leaving you grasping at straws, especially with minimal starting clues.
And as you dig deeper, ethical and legal questions loom, presenting a maze of moral considerations about how far is too far in the pursuit of knowledge.
But this mission, entrusted to me in 2021, was more than a revelation of the shortcomings of traditional search techniques.
It was an immersion into the depths of OSINT, identifying the nuanced tactics necessary to navigate through the digital clutter—tactics that need to be both effective and ethically guided.
I learned to decipher the complexities of the digital domain, sparking a broader dialogue on the transformative potential of these techniques in the relentless quest for information.
Now picture the stakes.
You cross paths with your dream girl at a sporting event, only for her to vanish into the crowd before you can muster the courage to speak. The digital world offers a lifeline to finding her again, if only you can navigate its depths.
And within the dense jungle of online content, transformative narratives wait to be uncovered, their potential to inspire and innovate buried beneath a deluge of information.
The implications for cybersecurity are profound.
Moreover, as our online footprints become increasingly complex, the challenge of digital forensics intensifies, demanding sophisticated tools to trace the intricate paths we leave behind.
This journey underscores the urgent need for advanced methods of information gathering, a need that has only intensified as our digital interactions expand.
Unlocking the Power of OSINT
During this mission, OSINT became my compass.
To put it simply, OSINT is a method that involves the collection and analysis of data from publicly accessible sources to gather intelligence.
I discovered that the information I needed wasn’t hidden in some dark corner of the internet; rather, it was there in plain sight.
The challenge was learning to see it, to sift through the noise and find the signals.
The concept isn’t new; Lt. Gen. Samuel V. Wilson, during his tenure at the American Defense Agency, astoundingly claimed that 90% of intelligence data came from open sources, a strategy that dates back to World War II.
Fast forward to today, technological progress has expanded the horizons of OSINT, making it an invaluable tool for researchers, journalists, and yes, even for everyday sleuths like you.
By mastering these specialized techniques, I was able to piece together the puzzle from the fragments available to me.
Beyond the Basics
When you explore public databases, engage in forums, and leverage specialized OSINT tools, you peel away layers of information that aren’t immediately obvious through conventional searches.
Each method you use enriches your OSINT toolkit, offering diverse avenues for intelligence gathering.
The Ethical Compass
As you navigate with OSINT, let ethics guide your path.
You must approach your quest with respect for privacy and adherence to legal frameworks.
You must handle the immense power of OSINT responsibly, ensuring that your pursuit of information respects privacy boundaries and legality.
Do not use this information to dox people.
Pioneering OSINT Techniques for Digital Exploration
Let’s explore four advanced OSINT techniques that I used to find that fugitive.
Each method serves a unique purpose, offers detailed steps for execution, and reveals specific kinds of information, helping to piece together digital footprints left behind by individuals.
1. Google Dorking
Google Dorking leverages advanced search operators to uncover specific data hidden across web pages. This technique is about sifting through online information to isolate the precise details you need, whether that be confidential documents or unsecured server data.
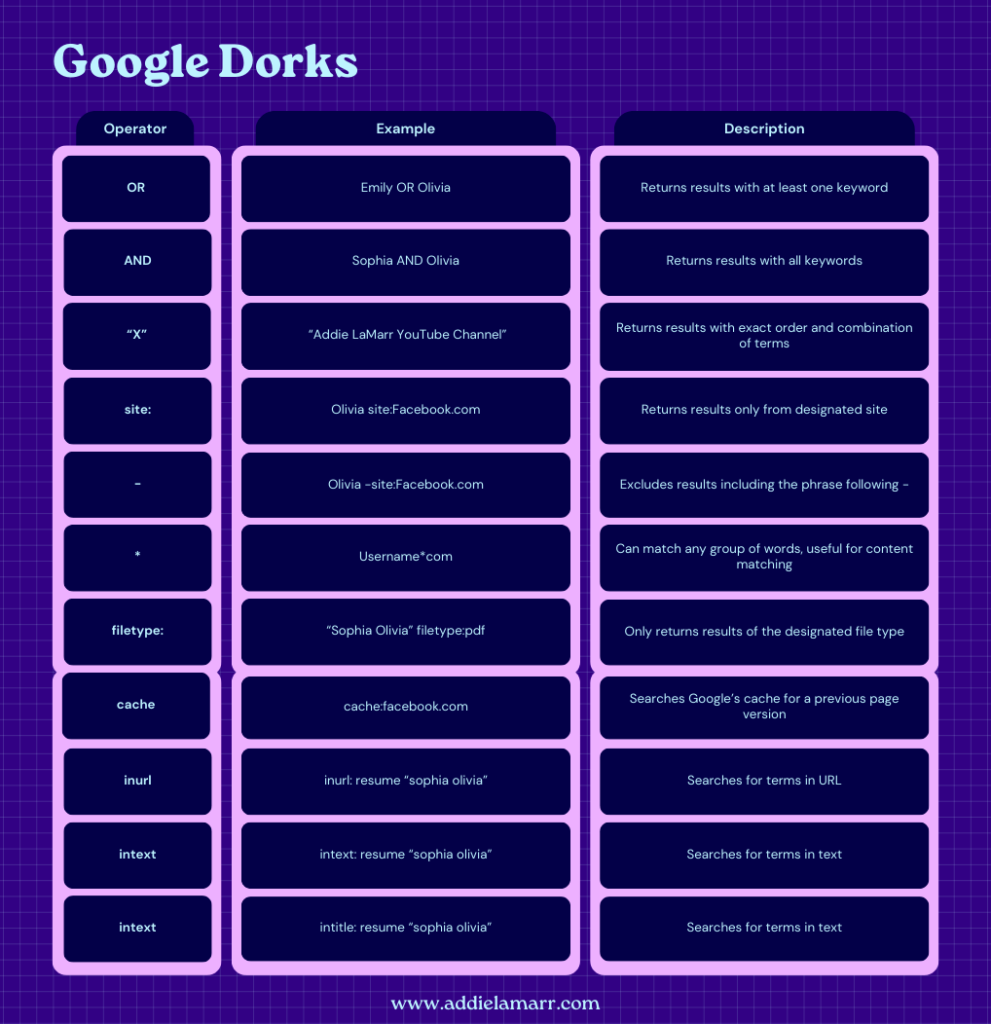
Here’s how to effectively employ Google Dorking:
- Open your web browser and navigate to the Google search page.
- Use advanced search operators like
site:,filetype:, andinurl:to refine your searches. For instance, typefiletype:pdfto locate PDF files. - Combine these operators with your targeted search terms to construct a detailed query.
- Review the results carefully, ensuring you respect privacy and legal boundaries by not accessing or downloading sensitive data without permission.
Limitations of Google Dorking include the potential for an overwhelming amount of data and the need for precise operator knowledge to filter effectively.
2. Reverse Image Search
This technique uses an image as a starting point to uncover a web of connected information, from identifying landmarks to tracing image origins.
Here’s how to use Reverse Image Search on platforms like Google Images and TinEye:
- Google Images:
- Visit Google Images.
- Click the camera icon in the search bar to choose ‘Search by image’.
- Paste an image URL or upload an image, then click ‘Search by image’.
- Explore the results to find related images or websites hosting the image.
- TinEye:
- Navigate to the TinEye website.
- Upload an image or paste an image URL.
- Review the results to trace the image’s web presence or locate similar images.
The limitation of Reverse Image Search lies in its dependency on the image’s online presence; if the image is not widely used or shared online, results can be limited.
3. Reverse Email Search
Reverse Email Search digs into the digital persona tied to an email address, revealing everything from social network profiles to website registrations.
Here are the steps to perform a reverse email search:
- Choose a reverse email search tool like Epieos.com.
- Enter the target email address into the search bar.
- Initiate the search to reveal linked online profiles or publicly available information.
- Analyze the results to gain insights into the individual’s digital presence and activities.
The primary limitation here is privacy regulations, which may restrict access to certain types of information.
4. Social Media Account Search
Delving into social media accounts provides a comprehensive view of an individual’s personal and professional life, revealing interests and connections.
Here’s how to conduct a thorough Social Media Account Search:
- Identify the relevant social media platforms (e.g., Facebook, Twitter, Instagram).
- Use the search function on each platform to enter the individual’s name.
- Apply filters such as location or workplace to narrow down the results.
- Examine profiles for pertinent posts, photos, and other information.
- Note any connections or patterns that emerge to build a detailed profile of the individual.
One limitation of this method is the variability of privacy settings across platforms, which can restrict access to certain information.
Understanding and applying these four OSINT techniques can greatly enhance your ability to gather and analyze information across various digital domains, though each has its limitations that must be navigated carefully.
Other Helpful Tips
- Finding email address related to a username: If you already have a username like HackerMan1, try searching ‘HackerMan1*com’ to discover if that username exists as an email on popular domains. It’s a smart move that can unveil email addresses that simple searches might miss.
- Uncovering new contact information from online documents: You have a powerful tool at your disposal: online documents. Use search parameters like ‘filetype:pdf’, ‘filetype:xlsx’, or ‘filetype:docx’ with the subject’s name to drill down into documents that might contain the contact information you’re after. These files are often overlooked treasures of detailed information, from contact lists to internal communications.
- Gaining network information through available email lists: To understand someone’s network, particularly if they’re part of groups or events you’re aware of, hunt for publicly available email lists. Queries like ‘filetype:pdf [domain] “email”‘ can lead you to email lists they’re included in, offering insight into their professional and social affiliations.
- Look through archived data and webpages: Don’t forget, social media platforms are filled with nuggets of personal data. The details shared in profiles and posts can piece together a digital persona that’s more telling than you might think. And consider the paths less trodden: archived web pages and data from breaches can be illuminating, revealing data that’s not visible on the current web.
- Keeping up with the information: As you gather this intel, keep rigorous records. Your documented trail is key to piecing together a coherent profile. Above all, navigate these searches with ethical precision. Privacy matters, and you must honor the boundary of personal information in your quest.
Completing the Mission
So, how did I use these OSINT techniques to find this man?
It all began with the seemingly insignificant image, a photograph of two individuals, that held the key to unraveling a man’s digital and physical whereabouts.
I just had to figure out who he was.
Starting with a reverse image search on the photo led me straight to its origin on Flickr—a jackpot discovery.
The beauty of Flickr, with its community of photographers, is that images are often tagged with locations and dates.
Multiple angles of the same event offer a wealth of context and data, enriching the find significantly.
This initial step helped me identify the event captured in the photo and the other person featured alongside my target.
Searching Flickr further for photos from the same event, I found additional images on that clearly depicted the person I was interested in.
Each image unearthed added a new layer to my understanding of his network and activities.
I found the social media profile of his associate in the original photo, which allowed me to search through his friend list to find him.

I scoured the Instagram followers list but didn’t see anything that looked like my target’s profile.
I went back to Flickr to try some more reverse image searches related to the target.
I finally struck it rich in the digital hunt: I managed to unearth his private social media accounts.
It seems he was quite taken with one of the shots I uncovered on Flickr.
So much so, that he’d chosen that very photograph—a snapshot from the same event captured by the photographer—and made it his own, proudly displaying it as his profile picture on his Facebook page.
Despite the initial frustration of encountering his locked-down privacy settings, fortune smiled on me — his relationship status wasn’t hidden.
That little oversight provided me with a direct link to his wife’s profile.
And what a find that was!
Her digital life was an open book; as an avid internet user, she left a vivid trail with her active podcast and social media profiles where privacy was a concept seemingly taken lightly, offering a bounty of information for the taking.
I now had their identity and completed most of my mission but there was one thing left to uncover.
Where exactly did they live?
Intriguingly, a photo on her podcast page, which showed her in their driveway with a car in the background, caught my attention.
The reflection in the car’s panel—a very distinct garage door—became my next vital clue.
Armed with the knowledge of their city from her social media profiles, I turned to Zillow to search for fancy neighborhoods where homes had similar garage doors.
Once I narrowed down the potential locations, I used Google Street View to explore these neighborhoods virtually.
By comparing specific details from the public family photos, such as identifiable landmarks and background features outside their home, I was able to pinpoint their exact residence.
From a vague photo to virtually standing outside the man’s house, the effectiveness of OSINT tools like Google Dorking, reverse image search, and social media analysis was undeniable.
Even for people with seemingly “private” accounts.
These tools allowed me to pull threads from the insane depths of the internet and weave them into a clear, comprehensive picture.
Your Turn
Now, imagine what you could uncover with the same tools and techniques.
Use these tools ethically and responsibly, and you too can uncover hidden connections and details that bridge the gap between the digital world and the physical one.
A wealth of information, previously hidden, now lies within your reach.
But developing proficiency in OSINT takes time and patience.
Begin with simpler searches and gradually integrate more complex strategies into your practice.
Experiment with different techniques to discover what yields the best results for your information needs.
The tools and methods for information gathering constantly evolve.
Keeping informed about updates to search engines, social media platforms, and OSINT tools will keep your skills sharp and effective.
In conclusion, OSINT transforms publicly available information into actionable intelligence.
By mastering techniques like Google Dorking, reverse image and email searches, and social media analysis, you open new doors to digital discovery.
Stay Curious,
Addie LaMarr
P.S. I’ve made the exciting decision to share my personal knowledge system and extensive notes with you, turning them into a living reference and resource. This is your invitation to gain a deeper understanding of the concepts I discuss and to see how they interplay within the broader technological ecosystem.
Currently in its formative stages, this repository will evolve to encompass over 1200 notes spanning topics like cybersecurity, blockchain, digital well-being, and other burgeoning technologies. These insights are the fruits of my 14-year journey in the tech industry, and now, they’re available to you, completely free of charge. Dive in and join me on this adventure of continuous learning and discovery.



Pingback: Empower Your Searches: Unleash the Hidden Powers of Google Dorking for Breakthrough Insights and Unrivaled Precision - Addie LaMarr
Pingback: OSINT: How I Carefully Hunted A Man - Addie LaMarr